Introduction
I’ve seen multiple customers struggling with their corporate information. Most of the time this data is secured in a traditional way without flexibility to collaborate.
Result: People find other way to collaborate: Dropbox, OneDrive, Box, Mails, Private-mails, whatsapp,..
You don’t want your personal data published on the web. Why do we allow organizations to be less secure with OUR information?
Goal: If you are curious about your data at this moment, setup a fast pilot traject. In 24 hours you will have real insights in your organization.
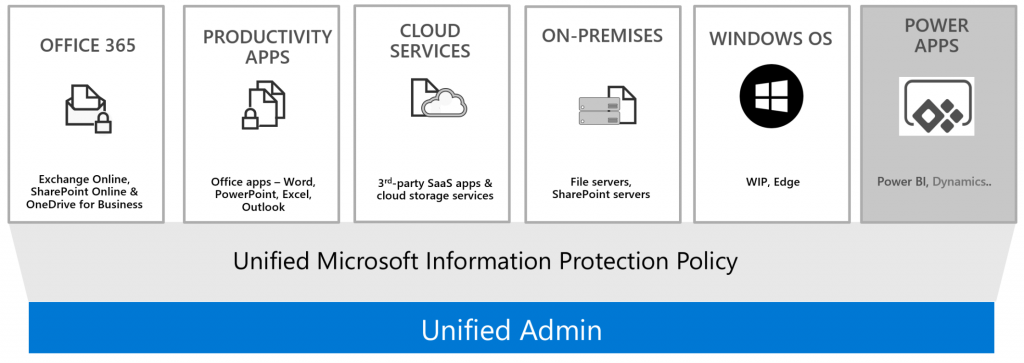
Environment: Office 365, Fileservers :-), Box, Dropbox. Connect!
What’s your strategy for protecting and governing sensitive and business critical data?
- Please comment if you managed to protect your data with a control mechanism. You have great insights and known your possible leakage.
Why should you work to protect information within corporate environments?
- Users are accidentally sharing information
- Users copying sensitive data for future use
- Organizations not knowing what they have and what’s exposed at this moment
- Users negligently sharing improperly with internal or external people
- Sensitive data has being accessed or stolen by unauthorized persons
- …
Use Microsoft native solution to discover your crucial data!
- Start with labeling of your information cross-platform to get actual insights!
- Labeling doesn’t mean it should be actionable – it’s just a state of reporting!
- later: classify, protect and monitor your sensitive data everywhere – cross platform.